Recommended videos
In this video, Chris Titus shows you how to secure a web server. The parts of the video are ufw setup, ssh keys, system modifications for networking, and checking which ports are open. Duration: 30 minutes.

In this video series, HackerSploit will be taking a look at how to set up, secure, and audit Linux servers. This video will explain and demonstrate how to set up and configure UFW and various firewall rules. Duration: 27 minutes.
In this video series, HackerSploit will be taking a look at how to set up, secure, and audit Linux servers. This video covers the process of configuring user permissions, assigning root permissions, and how to disable the root account. Duration: 19 minutes.

In this video series, HackerSploit will be taking a look at how to set up, secure, and audit Linux servers. This video covers the essentials of securing SSH. . Duration: 25 minutes.
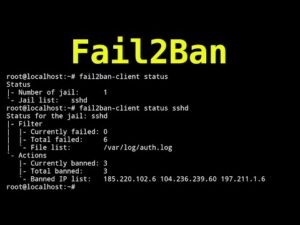
in this video HackerSploit will be showing you how to setup SSH brute-force protection with Fail2Ban on Linux. Fail2ban scans log files (e.g. /var/log/apache/error_log) and bans IPs that show the malicious signs -- too many password failures, seeking for exploits, etc. Generally, Fail2Ban is then used to update firewall rules to reject the IP addresses for a specified amount of time, although any arbitrary other action (e.g. sending an email) could also be configured. Duration: 24 minutes.

In this video series, HackerSploit will be taking a look at how to set up, secure, and audit Linux servers. This video will explain the process of securing Apache2.. Duration: 23 minutes.
